1. Introduction
The sectors of the economy, such as transportation, energy, healthcare, and finance, are becoming increasingly dependent on digital technologies in their core activities. The digital era creates vast opportunities and brings unparalleled economic growth, connecting businesses worldwide and supporting innovation. However, these interconnections have also exposed organisations and society to a constant threat of cyberattacks.
Cyberattacks are becoming more frequent and sophisticated throughout Europe. The surge in ransomware and cyberattacks increased by over 150% throughout the entirety of 2020. This signifies that cyber insurance is becoming a less profitable business for insurers [1]. According to forecasts, by 2025, as many as 41 billion devices worldwide will be connected to the Internet of Things. Therefore, decisive actions towards cybersecurity can enhance the credibility of digital tools and services, primarily ensuring the security of businesses operating in a cyber environment on a daily basis.
Ukrainian publicly traded companies, like many others worldwide, face the challenge of navigating the complex landscape of cybersecurity. The article presents the cybersecurity landscape of Ukrainian publicly traded companies, examining the threats they face, the measures they take, and the need for constant vigilance in the digital age.
The conducted analysis covers specific cases of cyberattacks, their complexity, economic consequences, and the financial market’s response. The overview of events underscores the role of geopolitical situations in shaping the market’s sensitivity to cyber threats.
The ultimate aim is to provide a comprehensive understanding of how cyber threats impact the stock value of Ukrainian companies and to indicate potential remedial actions for businesses facing increasing cyber risks.
1.1. The Essence of Cybersecurity and Cyber Threats
In today’s world, where technology plays a crucial role in all aspects of life, cybersecurity is becoming increasingly important for individuals, businesses, institutions, and nations seeking to effectively protect their digital assets from threats. It is worth noting that security is perceived as an objective state, characterised by the absence of threat, subjectively felt by individuals and groups [2]. In common understanding, security may denote a state in which an individual has a sense of certainty in a smoothly functioning legal and economic system. Security should not be treated as an independent variable, as it has a dynamic nature and can change due to complex phenomena [3].
Cybersecurity involves the resilience of information systems against actions that violate the confidentiality, integrity, availability, and authenticity of processed data or related services offered by these systems. The goal of cybersecurity is to secure information technology (IT) infrastructure, software, personal data, and ensure the integrity, availability, and confidentiality of information.
The communication space created by Internet-related linkages (cyberspace) is where processes threatening security are embedded. Cybersecurity threats are potential causes of incidents, and the vulnerability of an IT system is a characteristic that can be exploited by cybersecurity threats. According to the definition formulated by the US Department of Defense, cyberspace is a ‘global domain within the information environment consisting of the interdependent networks of information technology infrastructure (IT) and data contained therein, including the Internet, telecommunication networks, computer systems, and embedded processors and controllers’ [4]. Thus, cyberspace constitutes a kind of communication space created by Internet-related linkages [5]. Analysing the features of this cyber space indicates that it is a unique technosystem of global social communication, shaped by the integration of forms of information transmission and presentation, leading to digitalisation and the creation of a global integrated teleinformatics platform [6].
The opposite of security is a state of threat, the nature of which is associated with an objective category of risk that always exists independent of human awareness. Awareness of threat becomes a key decision criterion in every area of human and economic entity functioning, subject to management [7]. In the literature of economics and finance, risk is defined differently [8, 9]. Events in the geopolitical sphere confirm that risk is embedded in a dynamic evolutionary model of the world. Risk is associated not only with the realisation of specific intentions but also with the desire to maintain the existing state of affairs, that is, not taking or refraining from certain actions [10].
It is different from uncertainty, which relates to events or changes that are difficult to estimate, and the probability is completely unknown [11]. This phenomenon has caused the number and severity of cyber threats in recent years to be unprecedented, and the costs of cyberattacks for corporate boards and other external and internal stakeholders are enormous. The consequences caused in cyberspace by unauthorised users lead to dangerous social and economic consequences. Institutions and companies are taking initiatives to protect data, critical business processes, and the availability and integrity of information systems. The constantly evolving cyber threats, including those related to the armed conflict in Ukraine and the recent acceleration of digitisation, are key factors driving the need to develop appropriate tools to increase organisations’ capabilities in managing cybersecurity risk [12]. It is believed that cybersecurity needs to be incorporated at all levels of the company’s business model, that is, both in operational and supporting processes.
In Poland, a significant legal act regulating aspects of cybersecurity is the Act on the National Cybersecurity System. According to the Security Strategy of the Republic of Poland for the years 2019–2024, a cybersecurity threat is any potential circumstance, event, or action that may cause harm, disruption, or otherwise adversely affect networks and teleinformatic systems, users of such systems, and other individuals, in accordance with the Regulation (EU) 2019/881 of the European Parliament and of the Council of 17 April 2019 on the European Union Agency for Cybersecurity (ENISA) and on cybersecurity certification of Information and Communication Technology (ICT) products and repealing Regulation (EU) No. 526/2013 (the Cybersecurity Act).
According to the Threat Landscape Report – 2021 (ENISA Threat Landscape – 2021), the most significant cyber threats include the following:
ransomware software,
malicious software (malware),
email-related attacks,
threats related to data,
threats related to availability and integrity,
disinformation.
Vulnerability to cyberattacks is an objectively defined probability that the security system of an enterprise may be threatened. This indicates the likelihood of exploiting a gap in a specific security system. Refsdal et al. argue that cyber risk is not synonymous with every risk to which a cyber system may be exposed; cyber risk is limited to the risk caused by cyber threats [13].
The risk of server damage, such as flooding, is not a risk associated with cyberspace unless facilitated by a cyber threat. Examples of cyber threats include breaches of confidentiality through virus attacks in cyberspace and loss of availability due to denial-of-service (DoS) attacks.
The cybersecurity risk of an enterprise depends on various internal and external factors, including the size of the company’s assets, the technology it employs, vulnerability to threats, awareness and competence of employees in security matters, cybersecurity procedures, supplier (outsourcing) security, the vulnerability of the overall infrastructure on which the enterprise operates, and the motivation of potential criminals. Considering all these factors and the limited knowledge about the impact of individual factors on the overall enterprise risk, understanding, and estimating cyber insurance risk is very complex. Simple metrics, such as the number of lost records, do not always correlate with the total cost of risks [14].
1.2. Cybersecurity Challenges in Ukraine
Ukraine, emerging as an economic powerhouse in Eastern Europe, boasts a growing number of companies listed on stock exchanges. However, the country’s geopolitical situation has made it a primary target for cyberattacks. The ongoing conflict with Russia, which began in 2014, has complicated Ukraine’s cybersecurity landscape. Cyberattacks, often attributed to state-sponsored entities, target critical infrastructure, government agencies, and private sector entities.
Ukrainian publicly traded companies may be particularly vulnerable to these threats. They must confront a series of cybersecurity challenges, such as the following:
Phishing attacks, where cybercriminals use deceptive email messages and fake websites to persuade employees to disclose confidential information or install malicious software.
Ransomware attacks crippling operations and demanding high ransoms.
Vulnerabilities in supply chain security, as globalised companies rely on international supply chains, and cyberattacks on partners or suppliers can have a cascading impact on Ukrainian enterprises.
Politically motivated state-sponsored attacks that can result in significant financial damages.
Internal threats where employees may intentionally or unintentionally breach cybersecurity measures.
Ukraine has experienced various forms of cybercrimes, both related to the conflict with Russia and stemming from the overall rise in global cyber threats. These include hacking attacks on critical infrastructure, attempting to infiltrate energy systems, telecommunications, or air traffic management systems. Such attacks can have serious consequences for public safety and the functioning of the state. Another form of cybercrime is data theft and attacks on government institutions, where hackers seek illegal access to sensitive data, such as citizens’ personal information or classified government data. These attacks may be politically motivated, aiming to acquire confidential information or spread disinformation.
Financial systems are common targets for cybercriminals attempting to infiltrate banks and financial institutions to steal funds or manipulate financial systems. Ransomware attacks follow a similar pattern, infecting computer systems or networks and then demanding ransom in exchange for restoring access to data or systems. Companies, public institutions, and administrative entities may be targeted in such attacks. Attacks on the educational sector, such as schools, universities, and other educational institutions, are also prevalent due to the sensitive personal data of students and employees they store.
The Ukrainian government is taking actions to secure against these threats, but new cybercriminal techniques continue to emerge. Therefore, education, international collaboration, and continuous security system updates are crucial in combating these types of threats.
The extent and capabilities of non-state cyber actors became evident primarily during the Russian-Ukrainian war. According to Štrucl [15], the Russian Federation’s previously successful hybrid warfare strategies faced challenges in the initial months of the 2022 war due to the active involvement of various hacking and hacktivist groups aligning themselves with the conflict. In the Ukrainian context, there seems to be an unspoken agreement among state institutions to allow non-state cyber actors to selectively carry out cyber defence functions. In February 2022, Ukrainian Deputy Prime Minister M. Fedotov advocated for the establishment of the Information Technology Army of Ukraine. Hacktivist groups, such as Network Battalion 65, Elves, Cyber Guerrillas, Cloud Atlas, and notably, Anonymous, have been engaged in anti-Russian and anti-Belarusian activities, with Anonymous emerging as the most media-savvy cyber participant in the conflict [16].
1.3. Enhancing Cybersecurity Measures
In response to these threats, Ukrainian publicly traded companies increasingly recognise the importance of robust cybersecurity measures. Several strategies are employed to protect digital assets:
Organisations develop comprehensive cybersecurity policies and provide training to employees to raise awareness and promote best practices in cybersecurity.
Utilising high-quality software on end-user workstations, such as Endpoint Detection and Response (EDR) systems, helps secure and monitor computers, servers, and smartphones within the organisation. If any point in the IT system is infected, it is immediately isolated to prevent the attack from spreading to the entire corporate network and other devices.
Investments in advanced firewalls, intrusion detection systems, and endpoint protection are essential for safeguarding against cyber threats.
Developing and testing incident response plans is crucial for minimising the damage resulting from cyberattacks.
Companies conduct regular security audits and vulnerability assessments to identify and address weak points.
Collaborating with Ukrainian law enforcement and international partners can assist in effectively tracking and responding to cybersecurity threats.
Investing in employee education has a positive impact on the company’s security levels. Hackers often initiate attacks by sending messages to ordinary employees, because there is a significant chance that such a person will click on an infected link. Awareness of cyber threats among employees varies and is usually lower than that of IT specialists. Regular training sessions enable the elevation of knowledge levels and the adoption of best practices, enhancing employees’ resilience to hacker manipulations.
While these measures are essential, it is crucial to remember that the cybersecurity landscape is constantly evolving. Cybercriminals continuously develop new tactics and exploit vulnerabilities, requiring companies to maintain adaptability and vigilance. A proactive approach to cybersecurity is the most effective way to anticipate potential threats. Companies must also be aware of the regulatory environment. The Ukrainian government is working on cybersecurity regulations to strengthen legal frameworks for cybersecurity and data protection. Adhering to these regulations is not only a legal requirement but also a prudent cybersecurity practice.
Many studies show that cyberattacks, especially those directly targeting listed companies, cause significant damage [17]. This damage spreads throughout the industry [18]. As a result, investor confidence in such companies declines, the share price and hence the market value of the company falls, and share price volatility increases. There is usually a negative market reaction immediately after the attack [19]; the markets do not wait for the effects of such attacks to be determined. These are all negative phenomena. There is no positive market reaction to cyberattacks. In the long run, the situation can go one of the two ways: if the company tries to counter the attack, it can stay in the market [20]; technology companies are usually better prepared for attacks than companies in other industries [21]; if it does not take action, then it risks being taken out of the market [22].
2. Methods
The subject of the study is cyber threat events in Ukraine and their impact on the quotes and returns of the WIG_UKRAIN index during the period from December 2015 to December 2023 on the Warsaw Stock Exchange (GPW) S.A. Analyses conducted focus on the examination of cyber threat events in Ukraine and their impact on the WIG_UKRAIN stock index from 2015 to 2023. The evaluation includes the index’s return rates on the day of the cyber threat occurrence and the average return rate within sessions after the threat. According to the efficient market hypothesis, any event that could affect the valuation of financial instruments is discounted in the market price. Cyber threats are considered information that could potentially influence the value of financial instruments. Of course, cyber threats vary in type and scope of impact. Therefore, a review of selected cyber threats was conducted, and an assessment of their impact on the value of the Ukrainian companies’ index was made. The returns of the index were observed on the following events:
The day of the cyber threat occurrence.
The day immediately following the cyber threat occurrence.
The average return over five sessions following the cyber threat occurrence.
The performance of the WIG stock index was chosen as a reference point, for which corresponding returns were determined. During the period under review, the average volatility of the WIG_UKRAIN index quotations was compared with the WIG index quotations. Low rates of return were considered as the negative effect of reducing the value of Ukrainian-listed companies as a result of cyber activities. The WIG-Ukraine index is the second national index calculated by the stock exchange. It includes companies listed on the Warsaw Stock Exchange (GPW) whose headquarters or central offices are located in Ukraine or whose activities are predominantly conducted in this country. The first value of the index was published on 4 May 2011. Historical values of the index were recalculated from the base date of the index, which is 31 December 2010, when the index value was 1000 points. WIG-Ukraine is an income index, considering both prices of the stocks included and income from dividends and rights issues in its calculation.
On the other hand, the Warsaw Stock Exchange Index (WIG) encompasses stocks of companies listed on the primary market. It is the longest-standing index on the Warsaw Stock Exchange (GPW), calculated since 16 April 1991. WIG is an income-type index, meaning that its calculation takes into account both prices of the stocks included and income from dividends and rights issues. It also expresses the relative total value of the companies present on the Warsaw Stock Exchange (GPW) in relation to their value at the beginning of the index listing.
The main limitation of the research is the difficulty in determining the date of publication of information about a cyberattack. Several key dates there: the date of preparation of the cyberattack, the date of the cyberattack, the date of information about the cyberattack, and the date of reaching the market. Each of these dates is critical, but none can be determined with complete accuracy. It is often necessary to act on the basis of residual information. In addition, the number and nature of all cyberattacks are not known, so it is necessary to focus on a few.
3. Results
The onslaught of attacks on information systems using malicious software, such as ransomware, is immense, and furthermore, the size of the hacker arsenal is increasing. History shows that the actions of cybercriminals vary depending on the political, economic, and international situation in Ukraine. In most cases, these actions aimed to acquire confidential information related to Ukraine’s politics, defence, or economy.
3.1. Examples of Cyberattacks on Ukraine
Examples of cyberattacks have been compiled in Table 1.
Table 1.
Examples of cyberattacks on Ukraine.
[ii] https://stinet.pl/ukraina-historia-cyberatakow-cz-1-2/. [Accessed: Dec. 30, 2023]; https://www.gazetaprawna.pl/wiadomosci/swiat/artykuly/8333044,ukraina-hakerzy-atak-strony-rzadowe.html. [Accessed: Dec. 30, 2023];
[iii] https://www.money.pl/gospodarka/cyberatak-hakerow-na-ambasady-w-kijowie-wykorzystali-oferte-sprzedazy-samochodu-6918742318898016a.html. [Accessed: Dec. 30, 2023]; https://www.pap.pl/aktualnosci/news%2C1089376%2Czmasowany-atak-hakerski-na-ukrainie-nie-dzialaja-strony-
[iv] wielu-organow. [Accessed: Dec. 30, 2023].
Among the cyberattacks on Ukraine, actions with a sabotage character have been documented. These attacks were carried out to disrupt the normal functioning of critical infrastructure systems, such as power plants, energy systems, or telecommunications. Cyberattacks have intensified significantly since Russia declared war on Ukraine. The DDoS attack from February 2022 is considered the largest to date in Ukraine. Many Ukrainian websites, such as those of banks, government, and the military, were inaccessible. Temporarily, the websites recovered within a few hours. Such actions indicate an intention to instigate panic. This type of attack is aimed at disorganising the military, disrupting communication, and manipulating information.
3.2. The impact of cyberattacks on the volatility of the WIG_UKRAIN index
Some attacks aimed at disrupting the normal functioning of the government, creating chaos in society, or undermining trust in public institutions. The consequences of such actions involve not only manipulating information but also influencing public opinion at home and abroad.
It is worth emphasising that the motives behind attacks on Ukraine were complex and involved a combination of different objectives. Moreover, the scale and type of attacks change depending on the developments on international stage.
Figure 1 depicts the performance of the WIG_UKRAIN and WIG indices. Selected cyberattacks are marked with red arrows. The trends in which both indices were examined are generally in agreement. The correlation coefficient for the levels of quotations in the examined period is 0.3369. Its not very high value is primarily influenced by the period after Russia’s aggression on Ukraine when initially both indices lost value. However, since the end of 2022, the WIG index entered a strong upward phase, while the WIG_UKRAIN index continues to lose value. It is challenging to expect an increase in the value of the index of Ukrainian companies operating in such difficult times under uncertain political and economic conditions.
Figure 1
Performance of the WIG_UKRAIN and WIG indices from December 2015 to December 2023. Explanations: left axis – WIG_UKRAIN; right axis – WIG.
Source: Own compilation based on Warsaw Stock Exchange (GPW) data.
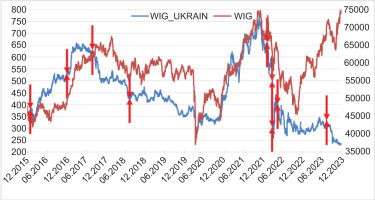
Table 2 presents return rate statistics during the period of a cyberattack and the period following the cyberattack. Throughout the entire period, the WIG_UKRAIN index experienced an average decrease of 0.0020% per session, while the WIG index saw an average increase of 0.0309% per session. The provided statistics allow for the distinction of two sub-periods, that is, until 2022 and from 2022 onwards. Before 2022, the changes were not as significant as they were after 2022. Generally, the commencement of military actions in 2022 significantly increased the volatility of WIG_UKRAIN index quotations, which is an expected situation, as markets tend to react poorly to uncertainty.
Table 2
Return rate statistics
Cyberattacks in Ukraine until 2022 did not inflict significant damage on the value of the index of Ukrainian companies. The attack on the energy sector conducted on 17 December 2016 caused maximum damage to the index. In this case, the statistics of the WIG_UKRAIN index compared to WIG look significantly worse. Any other highlighted cyberattack in the period until 2022 did not result in a permanent loss of value for the WIG_UKRAIN index, compared to WIG. One could even say that the market did not react to such cyberattacks. Moreover, even the attack on 27 July 2017, which was considered the largest in history at that time, remained practically unnoticed by the stock exchange.
The situation changed from 2022 onwards. With the onset of military actions, the stock market became significantly more sensitive to any information coming from Ukraine. The average change in the value of the WIG_UKRAIN index from February 2022 to the end of 2023 was -0.1195% per session. Meanwhile, during periods of intensified cyberattacks, especially the day after an attack, return rates reached significantly lower values. Only the attack on 12 July 2023 had a minor impact, but it was an attack without significant economic importance. However, every attack with potentially severe economic consequences from 2022 contributed to decline in the value of Ukrainian-listed companies
4. Conclusions
The global geopolitical situation plays a significant role in shaping global financial markets. Financial market sensitivity refers to the ability to respond to various factors, such as changes in the economy, political events, volatility in commodity prices, or factors disrupting the sense of security in a country. Rise in international tensions, conflicts, international negotiations, and political changes particularly impact the sensitivity of the stock market. The geopolitical situation in Ukraine has exposed entities operating in the capital market to increased cyberattack risks. However, companies are increasingly aware of the importance of investing in cybersecurity measures to protect their operations, data, and reputation. Ukrainian-listed companies must maintain a proactive approach to cybersecurity, continually adapting to new threats and changing regulations. Collaboration with governmental and international entities, comprehensive employee training, and the implementation of advanced cybersecurity technologies are crucial in the current efforts to protect Ukraine’s economic well-being in the digital age.
A review of selected cyberattacks on Ukraine, characterised as sabotage, indicates that the primary targets were critical infrastructure, such as power plants, energy systems, and telecommunications. The intensity of these attacks has increased since Russia declared war on Ukraine. The attacks had complex motives, such as disrupting government operations, creating social chaos, and undermining trust in public institutions. The goals also involved disrupting the armed forces, interfering with communication, and manipulating information.
Disruptive cyberattacks have resulted in the hindrance of telecommunications and the Internet services, restricted access to financial resources, and disrupted flow of news, and historically, they have been demonstrated to cause the denial of access to essential utilities, such as electricity, heating, and water. For instance, an incident on 29 March 2022 targeted Ukrtelecom, resulting in a connectivity collapse to only 13% of pre-war levels, causing nationwide disruption. The dissemination of false information and propaganda, often executed through attacks on the media sector, has a destabilising impact by influencing the information landscape and limiting the public’s access to timely, trustworthy, and official information. This erosion of reliable information undermines trust in institutions through the manipulation of information. Furthermore, the compromise of data, including hacking and leaks facilitated by hacktivist groups, has led to the widespread publication of substantial volumes of organisational and individual data online, with potential unknown long-term consequences.
Cyberattacks not only led to information manipulation but also influenced public opinion both domestically and internationally. They stirred uncertainty, weakened trust in institutions, and affected societal stability.
An analysis of stock indices (WIG_UKRAIN and WIG) suggests that the market became more sensitive to information related to attacks from 2022 onwards, especially after Russia’s aggression against Ukraine. Before 2022, cyberattacks on Ukraine had no significant impact on the value of Ukrainian company indices, except for the attack on the energy sector in December 2016. The situation changed from 2022 onwards, where every potentially economically harmful attack contributed to the decline in the value of Ukrainian-listed companies. With the onset of military actions, the stock market reacted more dynamically to cyberattacks. The returns of Ukrainian-listed companies reached lower values in the days following attacks, indicating increased market sensitivity to events related to the conflict.
Based on the conducted analyses, it is concluded that cyberattacks on Ukraine had a significant impact not only on infrastructure but also on financial markets and public opinion, especially after the start of military actions. The observed dependency confirms the growing sensitivity of the stock market to events related to cybersecurity. The Ukrainian government is taking steps to secure against cyber threats; however, education, international collaboration, and regular system updates remain crucial in combating such attacks.
It is important to underscore the importance of the effectiveness of cyber defence by Ukraine in repelling attacks and/or mitigating their impact [23]. Ukraine bolstered the resilience of its national ICT infrastructure and cyber incident response prior to and during the war, in cooperation with allied governments and private companies [24]. Ukraine’s private sector has also largely contributed to this process [25]. This included activities to strengthen the cyber resilience of Ukraine prior to and since the 2014 and 2022 military invasions, and cooperation with the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) [26]. Ukraine’s preparation, recognising that it has been the subject of cyberattacks for many years, has involved private–public partnerships. With the outbreak of the war, private actors, such as Microsoft, Google, Amazon, and ESET, s.r.o., have publicly acknowledged the role played in terms of tracking and forecasting cyber threats [27], hosting of governmental data in the public cloud outside Ukraine, and other forms of collaboration by the Government of Ukraine to thwart cyber threats [28–31].

