1. Introduction
The ongoing war in Ukraine invigorated scholarly and policy debates about the role of cyber in modern warfare at the strategic and tactical levels because the escalation dynamic did not follow the expected pattern, from cyber to a conventional escalation ladder. Although the intensity of cyber attacks on Ukrainian infrastructure peaked in the early phase of the invasion, to everybody’s surprise it was not followed by a cyber Pearl Harbor. In Washington, this subsequently led to the reconceptualisation of cyber from a standalone tool of modern warfare to a critical amplifier of effects across domains. In this process an integrated approach to cyber emerged, particularly in the United States, and most notably was adopted in a recent U.S. Department of Defense ‘Cyber Strategy’ [1]. At the tactical level, the conflict has been devoid of major changes either in terms of the actors involved or the degree of inter-domain coordination. There seems to be a consensus among cybersecurity experts that the major novelty has been an unprecedented volume of attacks against European NATO members, with a higher share of these attacks accruing on Eastern European and Baltic countries.
This study contributes to the current debate about the effects of the war in Ukraine on the cyber domain by examining whether the Allies moved closer to the shared threat perception in cyberspace since the beginning of the war – the question fundamental for NATO’s cyber posture. This study is based on a computational text approach to comparing national cyber strategies for the four Allies that have updated their cyber posture since the beginning of the invasion: Latvia, Italy, the United Kingdom, and the United States. It shows that the saliency of the risk management paradigm vis-a-vis the threat prevention paradigm has increased in some of the European capitals since the invasion and this has subsequently contributed to a greater convergence of threat and risk perceptions within the Alliance. The novel methodology developed in this article can be easily extended to a larger sample to track the internal cohesion within NATO on cyber threat perception as more Allies update their strategies in 2024 and 2025.
The article begins a literature review, and then presents a computational text approach known as cosine similarity. It is based on an analogy with the distance between vectors in Euclidian space and the similarity of the content of the sections of cyber security strategies that focus on the discussion of threats, risks, and actors in cyberspace. The larger the overlap in the vocabulary used in the corresponding sections in the cyber strategies, the greater the convergence within the Alliance on threat perceptions in cyber. The empirical section utilises the fact that cyber strategies are usually enacted for the period of four to five years and thus when countries enact or update their strategies they face a similar threat environments, which may or may not translate into the same cyber posture. So, this study provides a novel empirical approach to evaluating whether the large-scale aggression against Ukraine increased or diminished the consensus within the Alliance. The key finding is that the transatlantic consensus on the key characteristics of the operational environment has increased as a result of new cyber strategies.
2. Literature Review
The rapidly growing open source literature on the cyber dimension of the war in Ukraine can be grouped into (1) tactical studies that have focused on threat environment, types of actors, volume of attacks, geographic distribution of targets, and the types of capabilities used by state and non-state actors and (2) strategic ones that provide a high-level overview of the strategic implications of the cyber capabilities in the future conflicts. The tactical level analysis conducted primarily by think tanks and the IT industry reached the same conclusion that Russia’s deployment of cyber capabilities has been haphazard and lacked cross-domain integration as well as cross-actor coordination. It resembled more the activities that were planned and carried out by unconnected networks of non-state actors who did not synchronise their activities with commanders in the theatre. The intensity of these activities picked and ebbed around high-level multilateral events outside Ukraine and the selection of targets outside Ukraine targeted those NATO and EU countries that provided stronger support to Ukraine. Although the geographic scope of the targets surpassed those of the pre-invention level, cyber capabilities have remained the same: DDoS attacks, phishing, malware, ransomware, whispers, hacking, and social engineering [2–9].
One of the unresolved puzzles of the tactical analysis is how in spite of the seeming lack of top-down organisation and/or planning of cyber offensive, the attackers have exhibited a remarkable restraint in the selection of targets outside of Ukraine territory, in such a way not to trigger multilateral or unilateral retaliation by NATO as a whole or some of its Allies. So far, all the ongoing cyber activity has been under the threshold of Article 5 and fortunately has not inflicted either economic or human costs to justify the ‘shooting war’ that President Biden warned Putin about. It is difficult to reconcile how the fragmented and unconnected attackers managed to calibrate the intensity of cyber offense in a way not to exceed the Article 5 threshold. Subsequently, the large-scale conventional military confrontation broke out in spite of ominous exceptions of cyber Pearl Harbor.
This triggered the reconceptualisation of strategic uses of cyber capabilities particularly in the United States. The unclassified summary of the Department of Defense Cyber strategy published in September 2023 re-conceptualises cyber capabilities from being able to generate strategic effects by themselves to the ones that amplify the effects of capabilities in other domains. Thus cyber should be integrated into other domains to achieve the desired effects. Achieving this goal requires further investment in offensive cyber capabilities as well as extending the cyber toolbox.
The United States was not the only country that has updated its cyber posture since February 24, 2022, the day of the large-scale invasion. The United Kingdom, three EU members – Latvia, Italy, have released new National Cyber Security Strategies (NCSS). Although most of these strategies received attention from the scholarly community in the corresponding country [9–12], there have been relatively few cross-country comparisons of these recent developments [13]. The goal of the analysis that follows is to address this void.
3. Methods
The research design leverages a cutting-edge computational text methodology to compare cyber strategies. Although this is not the first study to rely on computation text analysis, it is the first one to measure the convergence or divergence on a specific issue. For example, Shafqat and Masood [14] and Song et al. [15] use latent topic modelling to identify clusters of countries that have similar NCSS. The small sample size in this study (n=10) is the major constraint on directly applying topic modelling here. Therefore, this study instead utilises cosine similarity scoring to compare vocabulary surrounding threats, risks, and actors – the three most contested policy issues when it comes to finding a shared position with the Alliance. By comparing the vocabulary used before and after the large-scale invasion as well as across the four countries, it is possible to assess whether the internal coherence within the Alliance declined or increased since Feb 24, 2022. Cosine similarity scoring was introduced to natural language processing to measure the distance between different texts. Building on an analogy with the distance in Euclidean space, cosine similarity computes a dot product or the angle between two vectors. The values are bounded by 0 meaning that there is no similarity at all between the two texts and 1 means that the two texts are based on identical vocabulary. Words could be arranged in a different order, but two texts consisting of the same vocabulary will get the same scores [16, 17].
4. Results
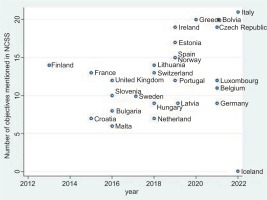
Before presenting cosine similarity scores, it is useful to highlight the diversity of cyber strategies of continental European Allies (see Figure 1). This figure was produced by the European Union Agency for Cybersecurity (ENISA) to provide a common yardstick for comparing approaches to cyber security within the European Union. It seeks to group strategies based on stated objectives. Although there has been an upward trend in the number of objectives mentioned in cyber strategies, there has been significant variation in the scope of objectives included in them, which makes systemic comparison across countries difficult because of different priorities reflected in the strategies. The objectives range from establishing a rapid response capability to balancing security and privacy and underscore the challenges for systematic comparisons across countries because these objectives are not consistently presented either over time or across the countries.
Figure 1
Number of cyber objectives in NCSS increases over time.
Source: Constructed by the Author from ENISA’s interactive map available at https://www.enisa.europa.eu/topics/national-cyber-security-strategies/ncss-map/national-cyber-security-strategies-interactive-map. [Accessed: Dec. 20, 2023].
Therefore, this study focuses on the sentences containing the keywords that appear persistently across the countries and over time: threat(s), risk(s), and actor(s). The extent of similarity or dissimilarity in the vocabulary used when discussing these terms provides insights into the evolution of intra-Alliance coherence over time, especially after the large-scale innovation. Sinc the large-scale invation, only four countries rolled out cyber strategy updates: Italy, Latvia, the United Kingdom, and the United States. The United States updated both the National Cyber Security Strategy issued by the White House as well as the Cyber Strategy published by the Department of Defense. Both of them were included in the study.
Table 1 compares how the discussion about threats, risks, and actors shifted over time. Both the United Kingdom and the United States White House strategies exhibited a high level of consistency over time in the discussion of these terms. This is surprising because of the changes in the administration from President Donald Trump to President Joe Biden. More changes were observed in the DoD strategies, particularly, with respect to risks and actors involved. The carryover from the 2017 to 2022 strategy in Italy was comparatively low across all keywords.
Table 1
Cosine similarity scores before and after the invasion.
| Italy 2017 & 2022 | Latvia 2019 & 2023 | United Kingdom 2016 & 2022 | United States | ||
|---|---|---|---|---|---|
| White House 2018 & 2023 | DoD 2018 & 2023 | ||||
| Threat(s) | 0.49 | 0.84 | 0.97 | 0.92 | 0.80 |
| Risk(s) | 0.58 | 0.84 | 0.93 | 0.89 | 0.62 |
| Actor(s) | 0.48 | 0.48 | 0.93 | 0.83 | 0.68 |
Table 2 provides examples of sentences that were analyzed for each keyword for Italy to underscore the fundamental shifts in the complexity of the discussion surrounding the issues. If the 2017 strategy focuses on the concert measures, e.g. National Security R&D Center to deal with the threats, the 2022 focuses on the activities of the Intelligence Community to deal with cyber threats. Although both sentences propose a solution, the language is district. Thus, the computed cosine similarity scores capture well this shift in the context in which these key issues are discussed.
Table 2
Examples of excerpts from Italy’s Cyber Security Strategies.
Another peculiar difference between the 2017 and 2022 excerpts is the degree to which risks, threats, and actors are mentioned jointly in 2022 and in completely non-overlapping sentences in 2017. This can be used as an indicator of whether risks and threats are perceived as interchanging or not. Threat mitigation and risk management constitute two fundamentally different approaches to cybersecurity. Threat either exists or not, risk is always there but to a different degree. Threats comprise malign activities of state actors motivated by geopolitical considerations and cyber criminals driven by economic gains. Their activities threaten the interests of the general public and a diverse range of internet users. Resilience to cyber threats emerges as the result of the implementation of comprehensive measures that promote trust and societal awareness. Risk management entails coordinating and integrating across sectors the same approach to risk management, one that takes into account not only the presence of malign actors but also the growing importance of autonomous systems (e.g. AI) that impact both resilience and threat environment in new ways. Risk management requires coordination among different levels of government and sectors. [18, pp. 13–15].
Do the new strategies reflect a greater degree of congruence across the countries on threat and risk perceptions? In the aftermath of the large-scale invasion, both the EU and NATO have enhanced their cyber toolkit to provide assistance to the member states facing cyber attacks, while at the same time homogenising the level of cyber resilience across the Alliance. Table 3 reports cosine similarity scores for each of the countries. The diagonal scores are always 1 because they correspond to the correlation of the country with itself. Therefore, we focus below on off-diagonal terms. Panel A corresponds to the old strategies and Panel B to the updated ones. One of the striking features is that we see greater similarity across all indicators in the new strategies, with only one exception: the differences in the perception of actors between Latvia on the one hand and the UK and US White House strategy increased in the updated versions. Threats are the issue that has the highest level of similarity across the countries whereas actors have the lowest level of similarity. The results also point to the division between the military and civilian approaches to cyber security. The US White House strategy is more similar to the one of the UK rather than to the U.S. DoD’s strategy. Overall, Table 3 suggests that although strategies are becoming longer and more comprehensive in terms of their objectives trans-Atlantic discussions of threats, risks, and actors are becoming more homogeneous. And this is a great news for the Alliance.
Table 3
Cross-country comparison of threat, risk, and actor description.
[i] Source: Cosine similarity results were computed by the author using the scikit-learn package for Python, after extracting sentences containing relevant keywords and grouping them into text blocks based on year and country, See Table 1.
5. Conclusions
NATO’s cyber posture has been evolving rapidly since the large invasion along the threat prevention trajectory. The Vilnius summit became a major milestone in this regard. It established an incident response facility to which 11 Allies have already contributed. To avoid the moral hazard problem mentioned above, it also introduced a verification mechanism to ensure that the Allies continue investing in their own cyber capabilities and established ways to enhance private R&D in cyber security by creating the Defense Innovation Accelerator for the North Atlantic (DIANA) funding mechanism [19]. This is also happening at the same time that the EU level cyber security mechanisms are evolving. The EU’s Strategic Compass adopted in March 2022 seeks to enhance ‘through capacity building, capability development, training, exercises, enhanced resilience and by responding firmly to cyberattacks against the Union, its Institutions and its Member States using all available EU tools.’ It aspires to strengthen the EU strategic autonomy in cyberspace ‘to protect, detect, defend and deter against cyber attacks’ [20].
This is happening at a time when the consensus within the Alliance on the threats, risks, and actors is growing. Although we cannot attribute any causality between these two important trends, we have to be mindful of the importance of common threat perceptions and the assessment of the operational environment in the cyber domain. This study applied a novel methodology to quantify the trends within the Alliance in the discussion of threats, risks, and actors involved and found that recently adopted cyber strategies point to greater consensus on cyber issues than before the full-scale invasion.

